Below is a listing of all the more commonly used Windows shortcut keys for every version of Microsoft Windows. If you are looking for shortcut keys related to programs in Windows, like Microsoft Word, Excel, Internet browsers, and others, see our 'Other computer keyboard shortcuts' page linked below.
BUT, a real system invokes overhead for every context switch, and the smaller the time quantum the more context switches there are. ( See Figure 6.4 below. ( See Figure 6.4 below. ) Most modern systems use time quantum between 10 and 100 milliseconds, and context switch times on the order of 10 microseconds, so the overhead is small relative to. Undoubtedly, the most popular name CCleaner is the ultimate choice to clean your PC & optimize it in just a few clicks. But you must be wondering why a cleaning tool is included in this list. Many of us know that the application is best known for quick startup, safe browsing, registry optimization, and much more.However, the tool is packed with some lesser-known features as well. Context Switches.; 2 minutes to read; In this article. The scheduler maintains a queue of executable threads for each priority level. These are known as ready threads. When a processor becomes available, the system performs a context switch. The steps in a context switch are: Save the context of the thread that just finished executing. Contexts 3.7.1 – Fast window switcher. Contexts Cracked Utilities. Contexts is a radically faster and simpler window switcher. It gives you 4 ways to switch windows: Switch with one click to any window: An auto-hiding sidebar shows your windows organized in groups. To switch to a window just click its title in the list. The ability to do context switching is an essential component for any multitasking OS. The same type of things that cause context switching in Linux would cause context switching in Windows as well. All a high thread count means is that the CPU will be forced to switch contexts more often to fulfill the processing requirements of the scheduler.
General Windows keyboard shortcuts
Alt+Tab
Switch between open applications in all versions of Windows. Reverse the direction by pressing Alt+Shift+Tab at the same time.
Ctrl+Tab
Switches between program groups, tabs, or document windows in applications that support this feature. Reverse the direction by pressing Ctrl+Shift+Tab at the same time.
Alt+double-click
In Windows 95 or later, display the properties of the object you double-click. For example, doing this on a file would display its properties.
Alt+Print Screen
Create a screenshot only for the active program window in all versions of Windows. For example, if you opened the calculator and pressed these shortcut keys, only the calculator window would be created as a screenshot. If the Print Screen key is pressed alone, the whole screen will be made into a screenshot.
Ctrl+Alt+Del
Open the Windows option screen for locking computer, switching user, Task Manager, etc. in later versions of Windows. Pressing Ctrl+Alt+Del multiple times reboots the computer.
Ctrl+Shift+Esc
Immediately bring up the Windows Task Manager in Windows 2000 and later.
Ctrl+Esc
Open the Windows Start menu in most versions of Windows. In Windows 8, this opens the Start screen and in Windows 3.x, this opens the Task Manager.
Alt+Esc
Switch between open applications on Taskbar in Windows 95 and later.
Alt+Spacebar
Drops down the window control menu for the currently open Windows program in Windows 95 and later.
Alt+Enter
Opens properties window of selected icon or program in Windows 95 and later.
Shift+Del
Permanently delete any file or another object without throwing it into the Recycle Bin in Windows 95 and later.
Hold down the Shift key
When putting in an audio or data CD that uses Autoplay, holding down the Shift key prevents that CD from playing.
Windows function key shortcuts
Below is a listing of keyboard shortcuts that use the keyboard function keys. See our what are F1 through F12 keys page for a full listing of what function keys do with all other programs.
F1
Activates help for current open application. If you're at the Windows desktop, this activates the help for Windows.
F2
Renames a highlighted icon, file, or folder in all versions of Windows.
F3
Starts find or search when at the Windows desktop in all versions of Windows.
F4
In Windows 95 and later, F4 opens the drive selection or address bar when browsing files in Windows Explorer.
- Pressing Alt+F4 closes the current open program window without a prompt in all versions of Windows.
- Pressing Ctrl+F4 closes the open window in the current active window in Microsoft Windows. Only works in programs that support multiple windows or tabs in the same program window.
F6
While in Windows Explorer, F6 moves the cursor to different Windows Explorer pane or in Windows 7 browse available drives.
F8
Pressing F8 over and over as the computer is booting starts the computer in Safe Mode.
F10
Activates the file menu bar in all versions of Windows.
- Simulates a right-click on selected item, which is useful if right-click is difficult or impossible using the mouse.
Windows keyboard key shortcuts
Below is a listing of Windows keys that can be used on computers running Microsoft Windows 95 or later and using a keyboard with a Windows key. In the below list of shortcuts, the Windows key is represented by 'WINKEY.' Because not all these shortcuts work in every version of Windows, we've mentioned which versions of Windows support each shortcut key combination.
All versions of Windows
WINKEY
Pressing the Windows key alone opens or hides the Windows Start menu. In Windows 8, this opens or hides the Start screen. Carnage racing 1 0.
WINKEY+F1
Open the Microsoft Windows help and support center.
WINKEY+Pause / Break key
Open the System Properties window.
WINKEY+D
Display and hide the Windows desktop.
WINKEY+E
Open Microsoft Windows Explorer.
WINKEY+F
Display the Windows Search or Find feature.
WINKEY+Ctrl+F
Display the search for computers window.
WINKEY+L
Lock the computer and switch users if needed (Windows XP and above only).
WINKEY+M
Minimizes all windows.
WINKEY+Shift+M
Undo the minimize done by WINKEY+M and WINKEY+D.
WINKEY+R
Open the run window.
WINKEY+U
Open Utility Manager or the Ease of Access Center.
Windows XP
WINKEY+Tab
Cycle through open programs on the Taskbar.
Windows 7 and 8
WINKEY+1-0
Pressing the Windows key and any top row number key from 1 to 0 opens the program corresponding to the number of the program icon on the Taskbar. For example, if the first icon on the Taskbar is Internet Explorer, pressing WINKEY+1 would open that program or switch to it if already open.
WINKEY+(Plus (+) or Minus (-))
Open Windows Magnifier and zoom in with the plus symbol (+) and zoom out with the minus symbol (-).
- Press the WINKEY+ESC to close the Magnifier.
WINKEY+Home
Minimize all windows except the active window.
WINKEY+P
Change between the monitor and projection display types or how second screen displays computer screen.
WINKEY+T
Set the focus on the Taskbar icons.
WINKEY+Left arrow
Shrinks the window to 1/2 screen on the left side for side by side viewing.
WINKEY+Right arrow
Shrinks the window to 1/2 screen on the right side for side by side viewing.
WINKEY+Up arrow
When in the side by side viewing mode, this shortcut takes the screen back to full size.
WINKEY+Down arrow
Minimizes the screen. Also, when in the side by side viewing mode, this shortcut takes the screen back to a minimized size.
Windows 8
WINKEY+,
Peek at the Windows desktop.
WINKEY+.
Display the search for computers window.
WINKEY+L
Lock the computer and switch users if needed (Windows XP and above only).
WINKEY+M
Minimizes all windows.
WINKEY+Shift+M
Undo the minimize done by WINKEY+M and WINKEY+D.
WINKEY+R
Open the run window.
WINKEY+U
Open Utility Manager or the Ease of Access Center.
Windows XP
WINKEY+Tab
Cycle through open programs on the Taskbar.
Windows 7 and 8
WINKEY+1-0
Pressing the Windows key and any top row number key from 1 to 0 opens the program corresponding to the number of the program icon on the Taskbar. For example, if the first icon on the Taskbar is Internet Explorer, pressing WINKEY+1 would open that program or switch to it if already open.
WINKEY+(Plus (+) or Minus (-))
Open Windows Magnifier and zoom in with the plus symbol (+) and zoom out with the minus symbol (-).
- Press the WINKEY+ESC to close the Magnifier.
WINKEY+Home
Minimize all windows except the active window.
WINKEY+P
Change between the monitor and projection display types or how second screen displays computer screen.
WINKEY+T
Set the focus on the Taskbar icons.
WINKEY+Left arrow
Shrinks the window to 1/2 screen on the left side for side by side viewing.
WINKEY+Right arrow
Shrinks the window to 1/2 screen on the right side for side by side viewing.
WINKEY+Up arrow
When in the side by side viewing mode, this shortcut takes the screen back to full size.
WINKEY+Down arrow
Minimizes the screen. Also, when in the side by side viewing mode, this shortcut takes the screen back to a minimized size.
Windows 8
WINKEY+,
Peek at the Windows desktop.
WINKEY+.
Snap a Windows App to the sides of the screen. Pressing it multiple times switches between the right and left side of the screen or unsnap the app.
WINKEY+Enter
Open Windows Narrator.
WINKEY+C
Open the Charms.
WINKEY+G
Cycle through desktop gadgets.
WINKEY+H
Open Share in Charms.
WINKEY+I
Open the Settings in Charms.
WINKEY+J
Switch between snapped apps.
WINKEY+K
Open Devices in Charms.
WINKEY+O
Lock the screen orientation.
WINKEY+X
Open the Power User Menu, which gives you access to many of the features most power users would want to use such as Device Manager, Control Panel, Event Viewer, Command Prompt, and much more.
Windows 10
WINKEY+,
Peek at the Windows desktop.
WINKEY+A
Open the Windows 10 Action Center.
WINKEY+G
Open the Game bar. Only works if a game is running.
WINKEY+I
Open the Windows 10 Settings window.
WINKEY+S
Open the Windows Search utility.
WINKEY+X
Open the Power User Menu, which gives you access to many of the features most power users would want to use such as Device Manager, Control Panel, Event Viewer, Command Prompt, and much more.
Additional information
A network switch (also called switching hub, bridging hub, and by the IEEEMAC bridge[1]) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device.
A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model. Some switches can also forward data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches.[2]
Switches for Ethernet are the most common form of network switch. The first Ethernet switch was introduced by Kalpana in 1990.[3] Switches also exist for other types of networks including Fibre Channel, Asynchronous Transfer Mode, and InfiniBand.
Unlike less advanced repeater hubs, which broadcast the same data out of each of its ports and let the devices decide what data they need, a network switch forwards data only to the devices that need to receive it.[4]
Overview[edit]
A switch is a device in a computer network that connects other devices together. Multiple data cables are plugged into a switch to enable communication between different networked devices. Switches manage the flow of data across a network by transmitting a received network packet only to the one or more devices for which the packet is intended. Each networked device connected to a switch can be identified by its network address, allowing the switch to direct the flow of traffic maximizing the security and efficiency of the network.
A switch is more intelligent than an Ethernet hub, which simply retransmits packets out of every port of the hub except the port on which the packet was received, unable to distinguish different recipients, and achieving an overall lower network efficiency.
An Ethernet switch operates at the data link layer (layer 2) of the OSI model to create a separate collision domain for each switch port. Each device connected to a switch port can transfer data to any of the other ports at any time and the transmissions will not interfere.[a] Because broadcasts are still being forwarded to all connected devices by the switch, the newly formed network segment continues to be a broadcast domain. Switches may also operate at higher layers of the OSI model, including the network layer and above. A device that also operates at these higher layers is known as a multilayer switch.
Segmentation involves the use of a switch to split a larger collision domain into smaller ones in order to reduce collision probability and to improve overall network throughput. In the extreme case (i.e. micro-segmentation), each device is located on a dedicated switch port. In contrast to an Ethernet hub, there is a separate collision domain on each of the switch ports. This allows computers to have dedicated bandwidth on point-to-point connections to the network and also to run in full-duplex mode. Full-duplex mode has only one transmitter and one receiver per collision domain, making collisions impossible.
The network switch plays an integral role in most modern Ethernet local area networks (LANs). Mid-to-large sized LANs contain a number of linked managed switches. Small office/home office (SOHO) applications typically use a single switch, or an all-purpose device such as a residential gateway to access small office/home broadband services such as DSL or cable Internet. In most of these cases, the end-user device contains a router and components that interface to the particular physical broadband technology. User devices may also include a telephone interface for Voice over IP (VoIP).
Role in a network[edit]
Switches are most commonly used as the network connection point for hosts at the edge of a network. In the hierarchical internetworking model and similar network architectures, switches are also used deeper in the network to provide connections between the switches at the edge.
In switches intended for commercial use, built-in or modular interfaces make it possible to connect different types of networks, including Ethernet, Fibre Channel, RapidIO, ATM, ITU-TG.hn and 802.11. This connectivity can be at any of the layers mentioned. While the layer-2 functionality is adequate for bandwidth-shifting within one technology, interconnecting technologies such as Ethernet and token ring is performed more easily at layer 3 or via routing.[6] Devices that interconnect at the layer 3 are traditionally called routers.[7]
Where there is a need for a great deal of analysis of network performance and security, switches may be connected between WAN routers as places for analytic modules. Some vendors provide firewall,[8][9] network intrusion detection,[10] and performance analysis modules that can plug into switch ports. Some of these functions may be on combined modules.[11]
Through port mirroring, a switch can create a mirror image of data that can go to an external device such as intrusion detection systems and packet sniffers.
A modern switch may implement power over Ethernet (PoE), which avoids the need for attached devices, such as a VoIP phone or wireless access point, to have a separate power supply. Since switches can have redundant power circuits connected to uninterruptible power supplies, the connected device can continue operating even when regular office power fails.
Bridging[edit]
Modern commercial switches use primarily Ethernet interfaces. The core function of an Ethernet switch is to provide multiport layer-2 bridging. Layer-1 functionality is required in all switches in support of the higher layers. Many switches also perform operations at other layers. A device capable of more than bridging is known as a multilayer switch.
A layer 2 network device is a multiport device that uses hardware addresses, MAC address, to process and forward data at the data link layer (layer 2).
A switch operating as a network bridge may interconnect devices in a home or office. The bridge learns the MAC address of each connected device. Bridges also buffer an incoming packet and adapt the transmission speed to that of the outgoing port. While there are specialized applications, such as storage area networks, where the input and output interfaces are the same bandwidth, this is not always the case in general LAN applications. In LANs, a switch used for end-user access typically concentrates lower bandwidth and uplinks into a higher bandwidth.
Interconnect between switches may be regulated using spanning tree protocol (STP) that disables links so that the resulting local area network is a tree without loops. In contrast to routers, spanning tree bridges must have topologies with only one active path between two points. Shortest path bridging is a layer 2 alternative to STP that allows all paths to be active with multiple equal cost paths.[12][13]
Types[edit]
Form factors[edit]
Switches are available in many form factors, including stand-alone, desktop units which are typically intended to be used in a home or office environment outside a wiring closet; rack-mounted switches for use in an equipment rack or an enclosure; DIN rail mounted for use in industrial environments; and small installation switches, mounted into a cable duct, floor box or communications tower, as found, for example, in fiber to the office infrastructures.
Rack-mounted switches may be standalone units, stackable switches or large chassis units with swappable line cards.
Configuration options[edit]
- Unmanaged switches have no configuration interface or options. They are plug and play. They are typically the least expensive switches, and therefore often used in a small office/home office environment. Unmanaged switches can be desktop or rack mounted.
- Managed switches have one or more methods to modify the operation of the switch. Common management methods include: a command-line interface (CLI) accessed via serial console, telnet or Secure Shell, an embedded Simple Network Management Protocol (SNMP) agent allowing management from a remote console or management station, or a web interface for management from a web browser. Examples of configuration changes that one can do from a managed switch include: enabling features such as Spanning Tree Protocol or port mirroring, setting port bandwidth, creating or modifying virtual LANs (VLANs), etc. Two sub-classes of managed switches are smart and enterprise managed switches.
- Smart switches (aka intelligent switches) are managed switches with a limited set of management features. Likewise, 'web-managed' switches are switches that fall into a market niche between unmanaged and managed. For a price much lower than a fully managed switch they provide a web interface (and usually no CLI access) and allow configuration of basic settings, such as VLANs, port-bandwidth and duplex.[14]
- Enterprise managed switches (aka managed switches) have a full set of management features, including CLI, SNMP agent, and web interface. They may have additional features to manipulate configurations, such as the ability to display, modify, backup and restore configurations. Compared with smart switches, enterprise switches have more features that can be customized or optimized and are generally more expensive than smart switches. Enterprise switches are typically found in networks with a larger number of switches and connections, where centralized management is a significant savings in administrative time and effort. A stackable switch is a type of an enterprise-managed switch.
Typical management features[edit]
- Enable and disable ports
- Link bandwidth and duplex settings
- Quality of service configuration and monitoring
- MAC filtering and other access control list features
- Configuration of Spanning Tree Protocol (STP) and Shortest Path Bridging (SPB) features
- Simple Network Management Protocol (SNMP) monitoring of device and link health
- Port mirroring for monitoring traffic and troubleshooting
- Link aggregation configuration to set up multiple ports for the same connection to achieve higher data transfer rates and reliability
- VLAN configuration and port assignments including IEEE 802.1Q tagging
- Network Access Control features such as IEEE 802.1X
- IGMP snooping for control of multicast traffic
Traffic monitoring[edit]
It is difficult to monitor traffic that is bridged using a switch because only the sending and receiving ports can see the traffic.
Methods that are specifically designed to allow a network analyst to monitor traffic include:
- Port mirroring – the switch sends a copy of network packets to a monitoring network connection.
- SMON – 'Switch Monitoring' is described by RFC 2613 and is a protocol for controlling facilities such as port mirroring.
- RMON[15]
These monitoring features are rarely present on consumer-grade switches. Other monitoring methods include connecting a layer-1 hub or network tap between the monitored device and its switch port.[16]
See also[edit]
Notes[edit]
- ^In half duplex mode, each switch port can only either receive from or transmit to its connected device at a certain time. In full duplex mode, each switch port can simultaneously transmit and receive, assuming the connected device also supports full-duplex mode.[5]
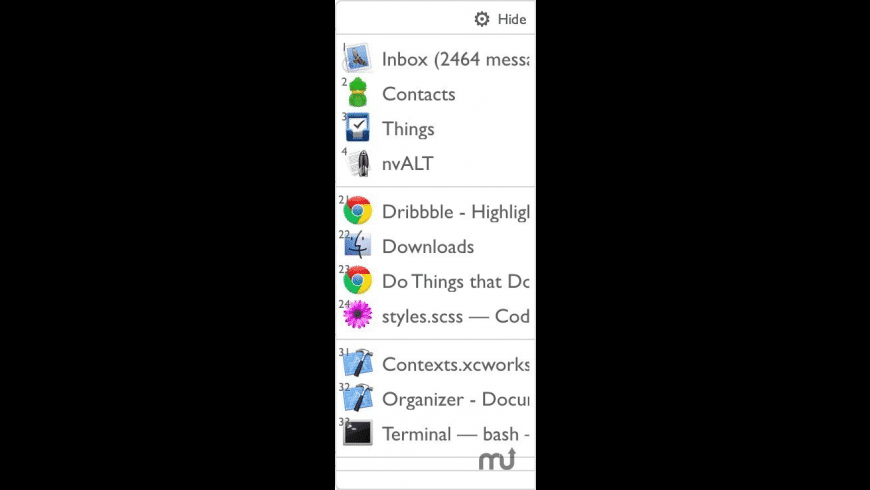
Contexts 3 6 1 – Fast Window Switcher Systems Diagram
References[edit]
- ^IEEE 802.1D
- ^Thayumanavan Sridhar (September 1998). 'Layer 2 and Layer 3 Switch Evolution'. cisco.com. The Internet Protocol Journal. Cisco Systems. Retrieved 2014-08-05.
- ^Robert J. Kohlhepp (2000-10-02). 'The 10 Most Important Products of the Decade'. Network Computing. Archived from the original on 2010-01-05. Retrieved 2008-02-25.
- ^'Hubs Versus Switches – Understand the Tradeoffs'(PDF). ccontrols.com. 2002. Retrieved 2013-12-10.
- ^'Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration'. Cisco Systems. 2014-03-31. Retrieved 2015-08-17.
- ^Joe Efferson; Ted Gary; Bob Nevins (February 2002). 'Token-Ring to Ethernet Migration'(PDF). IBM. p. 13. Archived from the original(PDF) on 2015-09-24. Retrieved 2015-08-11.
- ^Thayumanavan Sridhar (September 1998). 'The Internet Protocol Journal - Volume 1, No. 2: Layer 2 and Layer 3 Switch Evolution'. Cisco Systems. Retrieved 2015-08-11.
- ^Cisco Catalyst 6500 Series Firewall Services Module, Cisco Systems,2007
- ^Switch 8800 Firewall Module, 3Com Corporation, 2006
- ^Cisco Catalyst 6500 Series Intrusion Detection System (IDSM-2) Module, Cisco Systems,2007
- ^Getting Started with Check Point Fire Wall-1, Checkpoint Software Technologies Ltd., n.d.
- ^Peter Ashwood-Smith (24 February 2011). 'Shortest Path Bridging IEEE 802.1aq Overview'(PDF). Huawei. Archived from the original(PDF) on 15 May 2013. Retrieved 11 May 2012.
- ^'IEEE Approves New IEEE 802.1aq Shortest Path Bridging Standard'. Tech Power Up. 7 May 2012. Retrieved 11 May 2012.
- ^'Tech specs for a sample HP 'web-managed' switch'. Archived from the original on December 13, 2007. Retrieved 2007-05-25.CS1 maint: BOT: original-url status unknown (link)
- ^Remote Network Monitoring Management Information Base, RFC 2819, S. Waldbusser,May 2000
- ^'How to Build a Miniature Network Monitor Device'. Retrieved 2019-01-08.
External links[edit]
| Wikimedia Commons has media related to Ethernet switches. |
